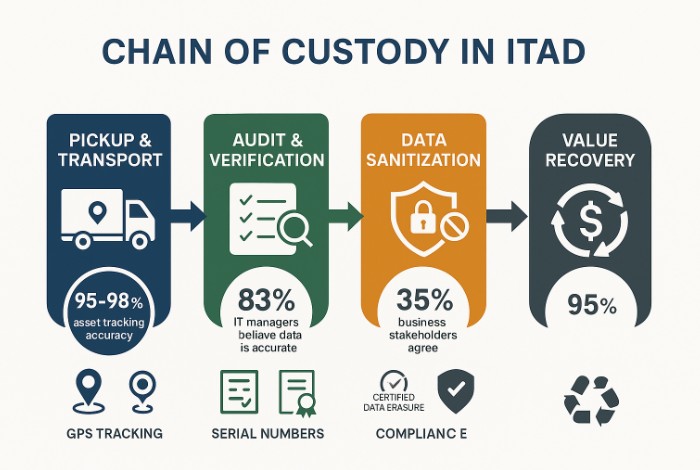
Picture this: A government ITAD company driver pleaded guilty to stealing and reselling government-issued IT devices that were scheduled for destruction, a real case from February 2025, according to the Department of Justice. Meanwhile, research reveals that 83% of IT managers believe their asset data is accurate, yet only 35% of the business stakeholders agree. These statistics highlight a critical vulnerability in IT asset disposition (ITAD): breakdowns in chain of custody protocols.
When organizations lack verified tracking systems, they risk data breaches, regulatory penalties, and asset theft. The most effective ITAD programs can track 95-98% of assets by matching serial numbers, while combining disposal tags with serial verification boosts accuracy by 99-100%.
Introduction to IT Asset Disposition (ITAD)
Importance of a Secure Chain of Custody
Chain of custody represents the documented, chronological record of IT assets from initial collection through final disposition, ensuring end-to-end accountability throughout the ITAD process. This critical framework protects organizations from data breaches, regulatory violations, and asset theft while supporting compliance with industry standards and legal requirements.
Modern enterprises face increasing pressure to maintain comprehensive audit trails for retired IT assets, particularly as data security threats evolve and regulatory frameworks become more stringent.
Ensuring Data Security
Data security considerations drive the fundamental requirements for chain of custody protocols in IT asset disposition. Organizations must implement comprehensive tracking systems that monitor every interaction with IT assets containing regulated or sensitive information.
Key security elements include:
- Asset identification through unique serial numbers and asset tags
- Personnel controls limit access to authorized individuals
- Documentation protocols for recording each transfer and handling event
- Verification procedures confirming asset status at every stage
- Audit capabilities to support compliance assessments and security reviews
The Health Insurance Portability and Accountability Act (HIPAA) and similar regulations mandate specific chain of custody requirements for organizations handling protected health information (PHI), making comprehensive tracking essential for regulatory compliance.
Regulatory Compliance Necessities
Regulatory frameworks increasingly emphasize the need for detailed chain of custody documentation during IT asset disposal.
Key regulatory requirements include:
- Sarbanes-Oxley (SOX): financial reporting and internal control mandates
- PCI DSS: Payment Card Industry Data Security Standards
- General Data Protection Regulation (GDPR): personal data handling requirements
- Industry-specific standards governing data security and IT asset tracking
- Federal and state disposal regulations require secure asset retirement
Failure to maintain proper chain of custody documentation can result in regulatory penalties, data privacy violations, and legal exposure.
Key Stages of ITAD Chain of Custody
Pick-Up and Transport
The chain of custody begins with secure pick-up and transport of IT assets from enterprise locations to processing facilities.
Transport security protocols include:
- GPS-tracked vehicles for real-time location monitoring
- Secure logistics procedures to protect equipment during transit
- Documented transfer records to verify the chain of custody
- Personnel verification to ensure authorized handling
- Insurance coverage protecting against loss or damage
Certified ITAD providers offer transport services designed specifically for data-bearing devices and sensitive electronics.
Audit and Verification
Comprehensive audit and verification processes confirm asset identity and condition upon arrival at the processing site.
Verification steps include:
- Asset identification: matching serial numbers and asset tags
- Inventory reconciliation: validating received assets against pickup records
- Condition assessment: evaluating physical condition and functionality
- Data classification: identifying necessary sanitization procedures
- Systems updates: recording audit findings in asset tracking platforms
These procedures reduce discrepancies and ensure traceability throughout the ITAD lifecycle.
Data Sanitization Techniques
Data sanitization is the most critical phase in the ITAD chain of custody, requiring the irreversible removal of all data from storage devices.
Primary sanitization methods include:
- Logical data wiping: using certified software to overwrite storage media
- Physical destruction: shredding or crushing hard drives and media
- Degaussing: applying magnetic fields to erase data from magnetic storage
NAID AAA certification establishes verifiable standards for secure data destruction and should be used to validate vendor practices.
Value Recovery and Disposition
Strategic value recovery enables organizations to offset ITAD costs while preserving a secure chain of custody protocol.
Value recovery options include:
- Refurbishment: restoring equipment for resale or internal reuse
- Component harvesting: reclaiming parts for spare inventory
- Material recovery: extracting metals and reusable materials
- Certified recycling: working with R2 certified facilities
- Disposition documentation: maintaining records of asset value and sale proceeds
These activities support financial returns while maintaining full traceability throughout disposition.
Documentation and Certification Processes
Preventing Data Breaches
Comprehensive documentation serves as a primary defense against data breaches by providing complete visibility into asset handling and data destruction activities.
Documentation requirements include:
- Asset tracking logs that record every interaction with IT equipment
- Certificates of Data Destruction verifying complete sanitization
- Chain of custody forms documenting all transfers and handling events
- Audit trails to support compliance verification and security reviews
- Legal documentation that provides protection in the event of a data exposure claim
The Coca-Cola data breach, among similar incidents, underscores the importance of maintaining detailed records throughout the ITAD process.
Ensuring Regulatory Adherence
Adhering to regulatory frameworks requires systematic documentation of all ITAD activities to support compliance verification and audit readiness.
Compliance documentation includes:
- Regulatory mapping identifying applicable requirements for each asset type
- Process documentation outlining procedures and controls in place
- Training records demonstrating personnel competency and role-based awareness
- Audit reports documenting ongoing verification and inspections
- Corrective action plans that address deficiencies and outline improvement measures
Advanced Tracking Technologies
Benefits of Using Tracking Technologies
Advanced tracking solutions enhance chain of custody operations by delivering real-time visibility into asset location, condition, and handling status.
Key benefits include:
- RFID tracking for automated asset identification and location monitoring
- RFID scanning to enable fast, accurate inventory reconciliation
- Centralized tracking systems with audit-ready reporting features
- On-site logging for granular documentation of handling and processing
- ERP integration with existing IT asset management tools
Organizations leveraging these technologies report increased accuracy, efficiency, and improved compliance rates.
Implementing Regular Audits
Regular audits are essential for verifying the effectiveness of the chain of custody protocols and uncovering areas for process optimization.
Audit components include:
- Process reviews to evaluate procedures, security, and control measures
- Documentation audits confirming athe ccuracy and completeness of records
- Personnel assessments that evaluate staff training and compliance awareness
- Technology evaluations examining system performance and reliability
- Compliance testing to validate regulatory adherence and risk management efforts
Partnering with Certified ITAD Providers
Choosing the Right ITAD Partner
Vendor selection directly impacts the effectiveness of your ITAD chain of custody—affecting security outcomes, compliance risk, and data integrity.
Key partner qualifications include:
- Industry certifications, such as NAID AAA and R2 standards
- A robust security infrastructure that protects during every phase
- Technology platforms that support real-time tracking and reporting
- Regulatory expertise aligned with HIPAA, SOX, GDPR, and other standards
- Proven experience managing large-scale, audit-ready ITAD operations
OEM Source meets all these criteria, delivering certified ITAD solutions that reduce risk, ensure compliance, and safeguard sensitive data.
Training Personnel for Chain of Custody
Proper personnel training is a foundational element of effective chain of custody management. It ensures that every team member understands their responsibilities across all ITAD procedures.
Training programs should cover:
- Chain of custody workflows and documentation requirements
- Data protection protocols for handling sensitive IT equipment
- Regulatory compliance and the consequences of non-adherence
- Technology platforms used for tracking, verification, and reporting
- Incident response procedures to mitigate and report potential breaches
Comprehensive, role-based training reduces the risks of human error and supports consistent, compliant execution of ITAD policies.
Secure Your ITAD Chain of Custody from Start to Finish
When it comes to protecting sensitive data, maintaining compliance, and recovering value from retired IT assets, a rigorous chain of custody is essential. From pickup to final disposition, every step must be documented, traceable, and audit-ready. By partnering with certified ITAD providers and implementing secure tracking systems, enterprises can confidently mitigate risk, reduce liability, and uphold industry standards.
Ready to safeguard your IT asset lifecycle? Contact OEM Source’s certified ITAD experts to learn how our secure chain of custody solutions ensure end-to-end protection, full regulatory compliance, and operational peace of mind.
Frequently Asked Questions
How do you complete the chain of custody form?
Complete chain of custody forms by documenting asset details such as serial numbers, device types, and condition assessments. Record each transfer with signatures, dates, and times. Be sure to include the pickup location, transport details, and receiving facility information to maintain a full audit trail.
How is the chain of custody completed?
Chain of custody is completed by tracking IT assets from initial pickup through final disposition. Use asset tags and serial numbers to ensure accurate identification, document each handling stage, and maintain continuous oversight with OEM Source’s comprehensive services and reporting tools.
What are the four steps of the chain of custody in ITAD?
The four key stages include:
- Secure pickup and transport, including GPS-tracked vehicles
- Audit and verification of received assets against documentation
- Processing, including inspection, data sanitization, and final disposition
- Final documentation, including certificates of destruction and compliance logs
How do you prove the chain of custody was maintained?
You demonstrate chain of custody by maintaining complete documentation: signed transfer forms, asset tracking logs, destruction certificates, and audit trails. Advanced tracking technologies and strict protocols from certified partners like OEM Source further ensure end-to-end accountability.
Why is the chain of custody important in IT asset disposition?
Chain of custody ensures that every IT asset is securely handled, tracked, and documented from pickup through final disposition. It protects sensitive data, supports regulatory compliance, and prevents loss or theft. Without a documented chain of custody, organizations risk breaches, penalties, and gaps in audit readiness—especially during high-stakes ITAD events.